NIST published a report discussing the core logical components that make up a zero trust architecture (ZTA). Zero trust refers to an evolving set of security paradigms that narrows defenses from wide network perimeters to individual or small groups of resources. Its focus on protecting resources rather than network segments is a response to enterprise tends that include remote users and cloud-based assets that are not located within an enterprise-owned network boundary.
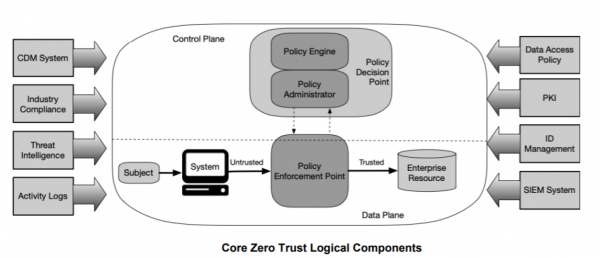
In addition to the core components in an enterprise implementing a ZTA, several data sources provide input and policy rules used by the policy engine when making access decisions. These include local data sources as well as external (i.e., nonenterprise-controlled or -created) data sources. For example, industry compliance system: this ensures that the enterprise remains compliant with any regulatory regime that it may fall under, including financial industry information security requirements. This includes all the policy rules that an enterprise develops to ensure compliance.
ZTA strategies are already present in current federal cybersecurity policies and programs, though the document includes a gap analysis of areas where more research and standardization are needed to aid agencies in developing and implementing ZTA strategies. Additionally, this document establishes an abstract definition of zero trust and ZTA as well as general deployment models, use cases where ZTA could improve an enterprise’s overall IT security posture, and a high-level roadmap to implementing a ZTA approach for an enterprise.

